‘Data’ is the new gold in today’s world,…. and Protecting it… is more important than ever.
One small security mistake can leak user data or open doors for hackers.
That’s when I understood why software security is important. Software security means protecting your software from hackers, bugs, and data loss.
More companies now make security a part of every step, so that users can trust them and the products that companies offer.
What Is Software Security?

Software security refers to the set of strategies and practices that safeguard software applications from unauthorized access and cyber threats.
These security risks can come from both outside (cyberattacks) or inside (such as coding mistakes or poor design). Therefore, you need good software security.
It helps keep
- data safe,
- prevents financial loss,
- and builds trust with your users
In simple words, it’s the shield that protects both the company and its users from digital threats.
If you’re building or maintaining software, understanding what is agile software and its approach to continuous testing can help you integrate security early in development.
What Are The Types Of Software Security?
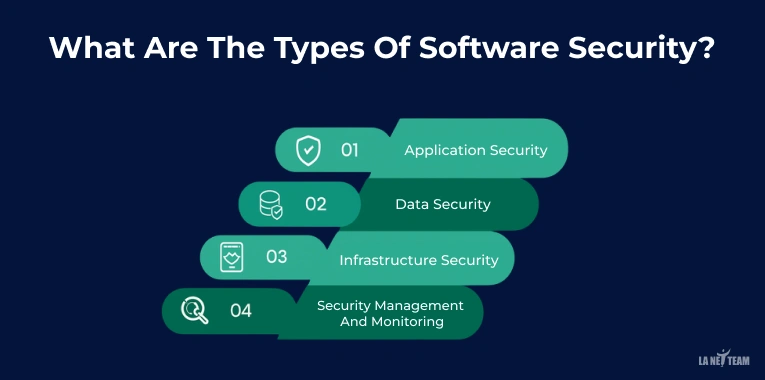
Knowing the different types of software security will help you protect your software from every angle. Each type you’ll read below focuses on a different area. Such as code, data, network, and the overall system.
Here are the four main types of Software security you should know:
1. Application security:
Application security deals with safeguarding the software against the threats during the development phase. This is in a bid to locate and remedy the vulnerability in the code, design, or setting before the attackers have the opportunity to strike.
Practices and tools:
- Application security testing (AST)
- Static application Security testing (SAST)
- Dynamic application security testing (DAST)
- Penetration testing
- Web application firewalls (WAF)
👉Read More: What is Custom Software Development?
2. Data Security:
Data security assists in the prevention of theft of sensitive or important information by unauthorized users. This kind of software security will make sure the data is correct, confidential and accessible to the right individuals.
Practices and Tools:
- Encryption
- Data loss prevention
- Access control
3. Infrastructure security:
Infrastructure security focuses on protecting the physical and virtual systems that support software.
Such as servers, networks, and cloud environments. It makes sure that the platform where the software runs stays safe from internal and external attacks.
Practices and tools:
- Network security
- Endpoint Security
- Cloud security
👉You can explore how DevOps as a Service helps automate infrastructure protection in modern setups.
4. Security Management and Monitoring:
Security management and monitoring focus on observing and maintaining the security of systems.
It helps in ensuring from any threats or suspicious activity. By detecting it and handling it before it causes harm.
Practices and tools:
- Vulnerability scanning
- Intrusion detection systems and intrusion prevention systems:
- Security information and event management
👉Read more: Guide to Software Development
Why is Software Security Important?
Protect sensitive data: We all know software often has private information of the users. Such as passwords, credit card details, or customer records.
Therefore, you need strong security, which helps in keeping data safe from hackers who might try to steal or misuse it.
Prevents cyber attacks: As cyber attacks continue to increase, hackers are increasingly becoming smarter and are exploiting the vulnerabilities of the software in order to penetrate. It is at this point that software security comes in, it complicates the hackers to get into your systems and destroy them.
Builds customer trust: Users trust companies that keep their data protected and safe with them. Keeping their data safe helps in building trust and makes users loyal towards the company’s product and services.
Avoid financial losses: A single cyber attack can cost a company with lot of money. And that’s why good security software is important, as it prevents these losses before they happen.
Protects the company’s reputation: Data being hacked from any company can affect and destroy their reputation.
Once people lose trust, it’s hard to win them back. This is where security software helps in maintaining a good brand reputation.
Best Tools for Software Security?
1. Patch Management
Who uses it: IT and security teams
A patch management tool helps in updating all your systems and apps with the latest fixes. By using this tool, you can stop hackers from using old bugs to break in.
Hackers often exploit unpatched software. Regular updates protect against known attacks and improve overall security.
2. Security training and awareness
Who uses it: All employees
Security training and awareness is one such program that assists in educating all the workers on how to identify and deal with security threats. The reason behind the practice is to sensitize all individuals within the organization about the risks that might occur and ways in which they could be circumvented.
Human error is a leading cause of security breaches. Awareness programs reduce mistakes and create a culture of vigilance.
3. Secure coding practices
Who uses it: Developers and software engineers
Secure coding practices refer to rules and tricks that developers use when coding to ensure that the software is inaccessible to the hacker and bugs. It is not an individual tool rather it is a combination of habits and approaches taken in the growth process to minimize security risks.
Software with fewer vulnerabilities is harder for hackers to exploit and reduces the need for costly fixes later.
4. Static application security testing
Who uses it: Developers and code reviewers
👉Learning how to become a software developer helps you understand secure coding from day one.
The SAST tool helps developers scan software code for security issues before the app goes live. It helps in preventing security flaws by finding them during coding.
Catching vulnerabilities during development is cheaper and safer than addressing them after deployment. It reduces the risk of introducing bugs that attackers could exploit.
5. Dynamic application security testing
Who uses it: Security teams and QA testers
DAST is a load testing of an application during its execution. It assists in analysing the behaviour of the app in real-life conditions to identify vulnerabilities instead of looking at the code.
It determines the existence of run time vulnerabilities which cannot be identified by utilizing a static analysis, to maintain the application safe in a live environment.
6. Web application firewalls
Who uses it: Security Administrators
WAF helps in protecting web applications from attacks originating from the internet. Additionally, it filters and monitors incoming traffic to block malicious requests.
Even well-coded applications can be vulnerable to unknown attacks. A WAF acts as a safety net to prevent web attacks in real time.
7. Intrusion Detection and Prevention Systems
Who uses it: Security teams and network administrators
IDS and IPS monitor your network. It alerts you to suspicious activity or blocks attacks automatically and helps you protect your system from intrusion.
They protect the network from attacks that bypass other security layers, such as malware, ransomware, or lateral movement by intruders.
8. Security Information and Event Management
Who uses it: Security analysts and incident response teams
SIEM tools combine security data from many sources, making it easier for analysts to see threats and respond fast. They help catch complex attacks early.
SIEM provides a holistic view of security, making it easier to detect complex threats that span multiple systems.
9. Vulnerability scanners
Who uses it: Security teams and administrators
Vulnerability scanners look for known flaws in systems and software. They help security teams find and fix weaknesses before hackers exploit them.
Regular scanning helps organizations stay ahead of attackers by identifying and fixing vulnerabilities before they can be exploited.
10. Authentication and authorization tools
Who uses it: Identity and access management teams
These manage who gets access to systems and what they can do, often with passwords, biometrics, or role controls. They prevent unauthorized access.
Even if an attacker obtains login credentials, strong authentication can stop unauthorized access.
Best Practices Of Software Security
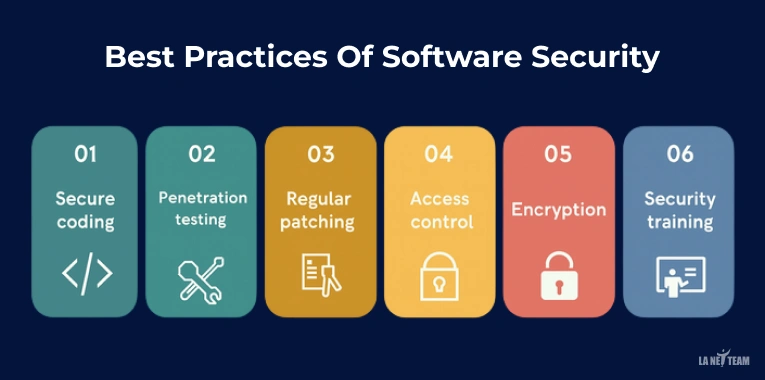
- Secure coding: This practice states that developers should write clean and safe code by using secure coding guidelines. They should also review and update their code regularly to fix any weaknesses that could lead to attacks.
If you’re using the best mobile app development software to build apps, secure coding should be a top priority to ensure your app remains safe and stable after launch. - Regular patching: Never leave all software, systems, and third-party tools without the latest patch. The majority of hackers take advantage of outdated software that is not patented. Being updated assists in sealing those security loopholes within a short time.
- Penetration testing: Does a regular penetration testing (or pen tests) to identify the vulnerable sides of your applications. This is just like in the real world, it is used to simulate the attacks and to ensure that the security measures that are in place are actually working.
- Access control: Limit who can access what. Use passwords that are difficult to crack, multi-factor authentication, and apply the least privilege principle according to which users can only be given access to what is actually required.
- Encryption: Prevent sensitive information by storing information and passing it through network encrypted. This makes sure that in case attackers acquire the information they are not able to read.
- Security training: Educate the staff on how to identify phishing emails, scams, and unsafe activities. Security awareness lessens the chances of human mistakes that normally contributes to the security breach.
👉To understand this better, explore modern software testing methodologies and how they connect with security checks.
Conclusion
Software security is one such tool that is utilized at the end of the day to foster the trust of the users.
Whenever one becomes a user, places an order or provides personal information, he/she is confident that the data is secure.
As cyberattacks are on the increase, and so are hackers, ensuring that trust is more than ever is more important.
Strong security, combined with a secure software development life cycle, builds lasting products.
